There are three steps to policy routing
1) Create an acl that matches the traffic that requires policy routing
2) Create a route map that specifies the next hop requirements
3) Apply a policy route map to the router inbound interface.
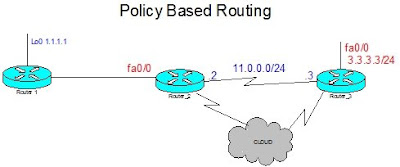
In this scenario the default route for traffic from R2 to R3 is over the frame relay cloud. The requirement here is to policy route ftp traffic originating from R1 1.1.1.1 to R3 3.3.3.3 over the point to point link between R2 and R3
Step 1 - create acl matching traffic
On R2
ip access-list extended 100
permit tcp host 1.1.1.1 host 3.3.3.3 eq ftp
permit tcp host 1.1.1.1 host 3.3.3.3 eq ftp-data
On R3
ip access-list extended 100
permit tcp host 3.3.3.3 eq ftp host 1.1.1.1
permit tcp host 3.3.3.3 eq ftp-data host 1.1.1.1
Step 2 - create route maps
On R2
route-map RICH
match ip address 100
set ip next-hop 11.0.0.3
On R3
route-map RICH
match ip address 100
set ip next-hop 11.0.0.2
Step 3 - apply pbr on incoming router interfaces
On R2 and R3
int fa0/0
ip policy route-map RICH
To verify the routing use the folowing commands
s ip policy
R3#s ip policy
Interface Route mapl
Fa0/0 RICH
To see the policy routing in action
debug ip policy

2 comments:
Maybe you should mention to use the "ip ftp source-interface loopback 0" on R1. Otherwise your ACL 100 would not match the traffic.
Yes thats a good point and worth highlighting. The ftp traffic needs to be sourced from the loopback on R1, and as such R1 requires this command.
Thanks for your comments.
Post a Comment